Microsoft Advanced
Threat Analytics
In the contemporary landscape, the discourse surrounding cybersecurity has transcended the confines of IT and data centers, now reaching the upper echelons of boardroom discussions. The frequency and severity of cyber-attacks significantly-ntly increased, showcasing a marked sophistication. Intruders often operate discreetly within a network for an average duration of eight months before their presence is identified. A prevalent trend in these attacks involves the compromise of user credentials, with attackers progressively favouring legitimate ITtools over traditional malware tactics.

Microsoft Advanced Threat Analytics (ATA) transforms network security by addressing the limitations of traditional IT tools. Designed for today’s sophisticated cyber threats, ATA offers a streamlined setup, rapid analysis, and clear threat information on an attack timeline. Leveraging deep packet inspection and data from various sources, including Security Information and Event Management and Active Directory, ATA constructs an Organizational Security Graph for real-time detection of advanced attacks. This intelligence-driven approach empowers organizations to proactively manage network security with agility and precision.
Microsoft Advanced Threat Analytics (ATA) is an on-premises platform designed to safeguard enterprises from advanced targeted attacks. ATA achieves this by automatically analyzing, learning, and identifying both normal and abnormal behaviors of entities, including users, devices, and resources


How ATA Works
ATA employs a proprietary network parsing engine to capture and analyze network traffic across multiple protocols (Kerberos, DNS, RPC, NTLM, etc.) for authentication, authorization, and information gathering. This data is acquired through:
- Port mirroring from Domain Controllers and DNS servers to the ATA Gateway
- Deployment of an ATA Lightweight Gateway (LGW) directly on Domain Controllers
ATA integrates information from diverse data sources, including logs and network events, to understand user and entity behavior within the organization. It builds a behavioral profile, receiving events and logs through methods such as SIEM Integration, Windows Event Forwarding (WEF), and directly from the Windows Event Collector (for the Lightweight Gateway).
Inserir
What ATA Does
ATA is equipped to detect various suspicious activities, concentrating on different phases of the cyber-attack kill chain, including:
- Reconnaissance: Gathering information about the environment, assets, and entities.
- Lateral Movement Cycle: Spreading the attack surface within the network.
- Domain Dominance (Persistence): Capturing information for the resumption of the campaign.
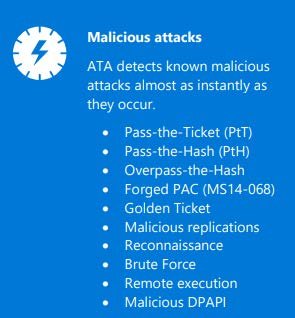
ATA categorizes its detections into three main types: Malicious attacks, abnormal behavior, and security issues and risks.
- Malicious Attacks: Deterministic detection of known attack types such as Pass-the-Ticket, Pass-the-Hash, and more.
- Abnormal Behavior: Identified through behavioral analytics and machine learning, covering activities like anomalous logins, unknown threats, and password sharing.
- Security Issues and Risks: Detection of broken trust, weak protocols, and known protocol vulnerabilities.
The ATA Console provides a clear view of Who, What, When, and How of the detected activities, offering a user-friendly dashboard for easy monitoring.
Sample ATA Screens:
- Pass-the-Ticket Attack
- Abnormal Behavior Alert
- Broken Trust Detection
The deploying Advanced Threat Analytics (ATA) serves as a crucial defense against sophisticated cyber threats. With ATA, your organization gains proactive detection capabilities, behavioral analysis for anomaly identification, and active defense against security risks. By investing in ATA’s security measures, your company enhances its resilience and readiness in the ever-evolving landscape of cyber threats.
